CaptainFreak Experience #1 - HacktoberFest 2018
Oh hello there, It’s your friendly neighbourhood hacker again :)
This raw post is supposed to be a documentation of my experiences in contributing to some of my favorite open source projects for HacktoberFest 2018.
Along the way I will try to give insights on how I did it, Expecting it might help someone kickoff and start learning from contributing to FOSS.
HacktoberFest 2018
Let’s start this with gentle introduction to purpose behind all of it. HacktoberFest (Hack + October + Fest) is an yearly celebration by Github for luring people into contributing to FOSS.
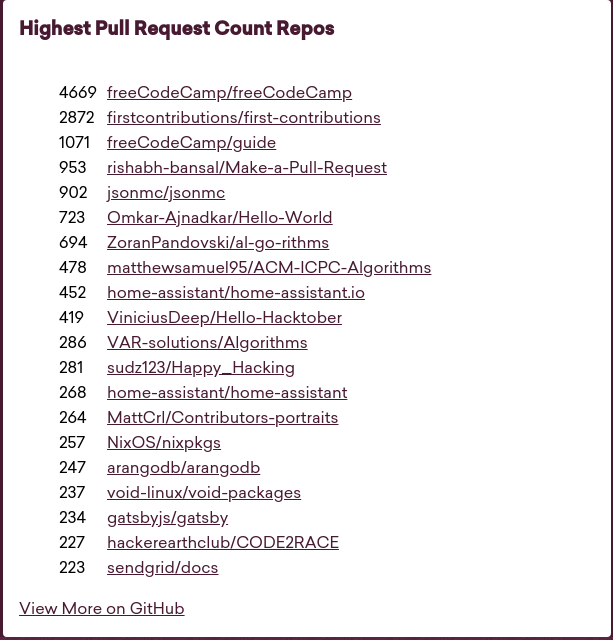
Github and sponsors of HacktoberFest offer a pretty T-shirt as swag to people who complete HacktoberFest challenge of submitting 5 non-spam Pull Requests to any of the FOSS project on Github. Well you can easily submit BullShit PRs and get that Github Swag as can be seen very clearly (〜 ̄△ ̄)〜
HacktoberFest’s swag is too pretty to be earned like this and also one shouldn’t miss on such good opportunity to learn and feel proud by contributing to the communities favorite projects. ¯\(ツ)/¯
Ok with all the ranting out of the way :P, lets get over with it.
GitDump
I started of small with contributing to a simple project which aims to be a plug before merging a PR commited with secret credentials(API keys, token, passwords etc) of third party service. If this commit histories with valid credentials are mined by an adversary, it can cause massive breaches/compromises and hence a hell lot of trouble for organizations. Small but useful script, enhanced it with some more keywords to look for.
PR : Link
Reconnoitre
As its description says, “A security tool for multithreaded information gathering and service enumeration whilst building directory structures to store results, along with writing out recommendations for further testing”. In a nutshell its a tool written in python to automate information discovery, more relevant on OSCP lab machines. Initially I wanted to contribute to its core functionality but ended up contributing a standard setup module.
PR : Link
NoSQLMap
Again its a python tool to automate detection and exploitation of NoSQL Injection Web Attack. Previously I had used it for checking my own written vulnerable code and even though its pretty robust tool, It wasn’t able to detect the context of injection which my code had. I had decided to someday contribute and enhance it to detect the injection in this context. What’s better time than HacktoberFest for this :). Looked into it again and found that it was getting stuck in some trivial loop before firing payloads. Fixed this bug and further will be trying to enhance it with some payloads.
PR : Link
Subfinder ♥
This is one of those tools which I or any of the hunters out there can’t live without. Respect 100. It’s a subdomain enumeration tool with tons of relevant and reliable passive sources of domain discovery and also bundles in bruteforce engine, resolvers etc. I was supposed to be contributing to it from its initial days but due to my incompatibility with Golang and other commitments, I couldn’t. But took a strike at it again with hacktoberfest. Took a hurried look over Golang for an hour and I was ready to contribute as it is very well structured tool with lots of modularity and it made me focus on logic flow instead of worrying about syntactic unfamiliarities. I added another passive source called Urlscan.io to it.
PR : Link
Metasploit ❤❤
Oh this tool should not require any introduction because that would be disrespect to it. But still for you suckers who don’t know, It’s a de facto penetration testing framework written in Ruby with 539+ payloads ready to shoot with 1800+ publicly disclosed exploits with 40+ encoders. Frameworks are meant to make the things easy, and I can’t think of another framework which beats Metasploit in that regards. Over that its very very well written, designed and structured piece of software with an extensive contribution guide. One of the best open source project and community. I can just go on and on praising it <3

I had used metasploit in the past but not very extensively and had not enumerated it’s all features. Still being naive, directly jumped into its massive codebase :P. I had not even written a simple Ruby program of puts "Hello Ruby" before. As expected failed miserably to understand it’s internals. Started off again from enumerating metasploit and learning Ruby. After that it was relatively clear. Found a simple issue of adding enhancement of TCP protocol to its SNMP Login Scanner along with its implementation of UDP. Learned a lot about project’s core, Ruby, SNMP, its use and its significance in information gathering for pentesting networks. Metasploit community is very strict regarding merging PRs, I guess it will take a lot of polishing before my PR gets ready to merge as it’s my first one.
PR : Link
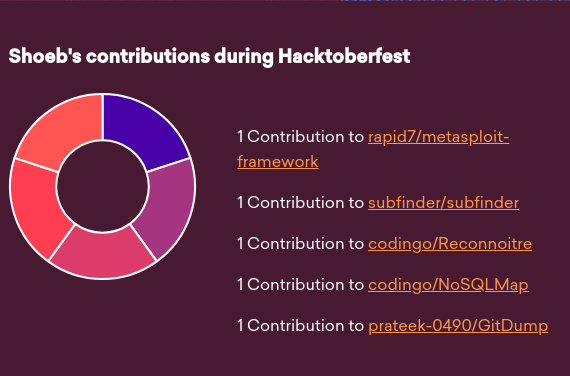
Ok, that’s it folks. It was very less time for such challenge to be completed but I tried, Maybe I could have tried harder. Anyway, October is still young. I would suggest to contribute to FOSS, earn knowledge and a bonus T-shirt with it. If you are not able to understand any of the mentioned things go to this Magical Link. I am still a script kiddie 😇 hence if you feel something is erroneous/inaccurate, feel free to comment below.
Shoutout to @hdmoore, @sinn3r, @Ice3man, @codingo_, @prateek, @rahuldhawan291, @manasmahapatra for all these awesome projects and help.
Cheers to Hackery and Growth,
CaptainFreak